Source of contribution: Beijing Tide Huizhi Technology Co., Ltd. (400-608-2988)
Current status of campus management
1. Use the gate channel with caution
Similar to the gate channel of the subway ticket checking system, it is not very suitable for installation at the campus entrance because there are several fatal problems.
First, the problem of injury to children, although there are a variety of electronic and mechanical anti-pinch measures, but there are still the possibility of pinching children, especially for children who are kindergarten or elementary school, causing unpredictable harm. .
Second, once the injury occurs at the school gate (the case of Fujian Nanping is outside the school gate), the child cannot enter the school quickly. Or once the injury occurs in the school, the child can not be quickly evacuated.
Third, the gate channel is generally not too high, it is easy to jump over, did not play a real role.
Fourth, the judgment of the gate channel relies on the obstruction of obstacles. The ability to prevent tailing is relatively weak, and the possibility of mixing in is relatively large.
2. The purpose of the technical product is to accurately discover rather than control
The current technology products are not able to automatically identify and automatically control people who are suspected, and it is not realistic to exclude 100% of suspects from campus. After all, it is not suitable to raise the walls and fingerprints. Used in school. This is too inefficient, time and application costs are too high and it is easy to reduce the vigilance of managers.
Therefore, the first direction of selecting a device should be accurate and fast identification, and a quick response.
3. The selection of actions after recognition is very important
After identifying the danger, an integrated approach should be taken to remove the danger. Isolation of suspects and children, intimidation of suspects, and immediate call for help will minimize the harm.
Suggested solution
Brief description of the working principle of campus access (channel): Through the four infrared probes on the channel, the direction of the entering and exiting personnel is judged, and the card reader on the channel issues a card reading signal, accepting the card information carried by the person entering the body, passing Computer software identifies it. When a legal person passes, there is no abnormality in the channel. When an illegal person passes, it cannot be recognized normally. The system will have an alarm and capture it through the camera and display it in real time on the computer in the administrator's office.
The campus access (channel) management system is coordinated and mutually coordinated by infrared detection, RFID technology, video surveillance, access control, alarm output, and video output, enabling humanization and intelligence of the entrance and exit control. The logic design of infrared detection determines whether the channel system can accurately record the entry and exit status of each person. The selection of RFID determines the effect of long-distance card reading. The functions that the channel system can implement can be described as: the channel infrared detector can accurately obtain the number of passes and the direction of movement, including the accurate judgment of various complicated situations (for example: 2 people come on the way, return halfway and pass immediately, The wearer's clothing has infrared reflection ability, the carrier carries long items, such as luggage, bicycle passing, etc. When the legal card passes, the entry and exit records can be used as the basis for the attendance analysis and statistics, and the video or snapshot can be set. The purpose is to compare whether the cardholder's appearance is consistent with the card registration, that is, check the card swiping phenomenon; when there is no card or illegal card, record or capture and alarm. The history includes a wealth of information: image screens, photos, directions of entry and exit, personal information, illegal information, location through the gate area, time (accurate to seconds).
In the control of entrance and exit and the safety management of people and property, safety and convenience are two contradictory and contradictory concepts. The high security level is bound to be inconvenient, and the barrier-free rapid identification channel is humanized in security products. One of the products, using technical means to bridge the contradiction between safety and convenience.
Security Management Design: The system enables monitoring and identification of every incoming and outgoing person (including legal identity and no card or illegal identity) and reacts quickly. The entry and exit records (including images) of the legal identity are stored in the back-end database, and the entry and exit records of any time period can be retrieved, and the entry and exit records of the sensitive time period are selected according to the management regulations, or all the entry and exit records of the sensitive personnel.
User-friendly design: The design of the barrier-free fast-track is designed to identify the entrances and exits with very large traffic (such as campus campus, shuttle attendance, long-distance express check-in, etc.). It is characterized by fast and accurate identification and does not require the person to stay. Because in the identification process, the main purpose of the system is to quickly and accurately screen illegal identities when most of the legal identities are passed, we have no reason to ask most legal identities to sacrifice time to cooperate with the inspection of illegal identities, but not because of this. Caused import and export congestion. Therefore, the design of the barrier-free channel is very important. It is a common application method to quickly and accurately determine the illegal identity when the personnel pass the barrier-free channel, and output the alarm signal. Moreover, the system can use the image comparison technology to make suspicious entry and exit records or suspicious during sensitive time periods. Personnel information is filtered. This is the organic combination of security management and humanized management, and it is also an effective embodiment of the true intention of managers.
System structure and principle
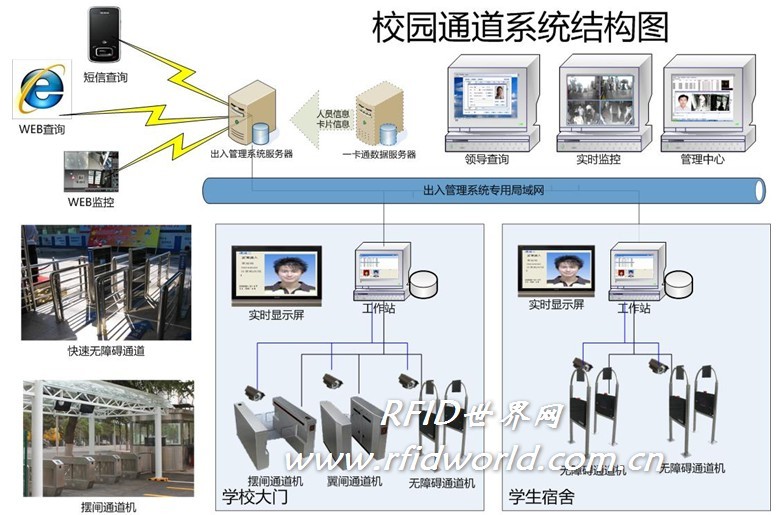
Structural schematic
The system uses distributed database management. All data exists in both the central database and the local database. When there is data change (such as account opening, loss reporting, account cancellation, etc.), the data is automatically synchronized through the network at each management station.
When the network or server fails, it does not affect the operation of the channel control system.
If the network or server fails, all data will be automatically stored in the management workstation database, and automatically retransmitted when the failure recovers.
Data transmission is verified by CRC check mode to ensure the correctness of data transmission.
Bitcoin mining is the process of creating new bitcoin by solving puzzles. It consists of computing systems equipped with specialized chips competing to solve mathematical puzzles. The first bitcoin miner (as these systems are called) to solve the puzzle is rewarded with bitcoin. The mining process also confirms transactions on the cryptocurrency's network and makes them trustworthy.
For a short time after Bitcoin was launched, it was mined on desktop computers with regular central processing units (CPUs). But the process was extremely slow. Now the cryptocurrency is generated using large mining pools spread across many geographies. Bitcoin miners aggregate mining systems that consume massive amounts of electricity to mine the cryptocurrency.In regions where electricity is generated using fossil fuels, bitcoin mining is considered detrimental to the environment. As a result, many bitcoin miners have moved operations to places with renewable sources of energy to reduce Bitcoin's impact on climate change.
Btc Miner,Bitmain S19 Xp,Bitmain Antminer S19 Xp,Antminer Bitmain S19 Xp 140Th
Shenzhen YLHM Technology Co., Ltd. , https://www.ylhm-tech.com