(Original title: Mysterious cyber worms appear, infecting tens of thousands of devices without sabotage, but against other Trojans)
Author: Xie unitary, Lei Feng network of network security.
Knowing that there is such a question:
If there are "super heroes" such as Wolverine and Spider-Man, do you think the world is getting better or worse?
Some people think that if a group of "righteous police" who believes in justice are required to maintain peace, then the world must have a legal system that breaks down. Some people think that if the real evildoers are in the spot, the emergence of a superhero must be a good thing.
This problem has no result because the real world may never have a superhero. However, cyberspace has really staged a similar scenario:
A malicious program called Mirai swept more than 1 million devices worldwide and launched arbitrary attacks on Internet devices. At its worst, it caused more than half of the United States to cut off the Internet (October 2016, a large-scale US off-network incident)
Just as everyone could do nothing about it, another peculiar program emerged. It spread quickly and without any damage. Instead, it sneaked out the infection channel of Mirai's malicious programs in the device and alerted people to safety.
No one knows where this fancy program came from. However, this is not the online version of the super hero movie plot?
A group of mutants with super powers (Mirai malicious program) is just as desperate as people are desperately helpless and desperate. Another group of superpowers appears to try to save people in distress...
This episode is no longer fun!

â–²X-Men poster (remembering the young wolves)
Everything has to start with a demon being unsealed...
Devil unblocks
On September 30, 2016, the enraged hacktivist Senpai released ç‰çˆirai, one of the most terrifying demons of the online world. On that day, security researchers around the world were crazy about it. A month later, the demon has infected more than one million devices worldwide, and the number is still rising sharply.
Mirai is actually just a small malicious program, but it will exist as a parasite in the device, continue to infect more devices, and manipulate the device to attack, one, ten, one hundred, continue to spread. Just like a zombie movie virus infection, one bite one, one bite one, and finally the zombie swept the world.
People named this type of worm program a "botnet".

â–² Botnets, pictures from the network
In some ways, Mirai is more terrible than the real zombie virus.
First of all, it is around you.
We often say that the future is the era of the Internet of Things and everything becomes smart. For botnets, it will be a feast. All networked devices in your home, such as webcams, smart TVs, smart locks, telephones, routers, lights, routers, etc., may become "prey" for the Mirai botnet.

â–² smart home, picture from the network
Secondly, the Mirai botnet also has a powerful "rebirth" feature. You have just cleared the Mirai virus on your infected device and may be reinfected by other "zombie" in less than a minute.
The most frightening thing is that the zombies in the movie do not have a unified command and do not engage in conscious and focused attacks. However, behind the Mirai botnet there are manipulators who can control thousands of infected devices to attack a target. Formed the "zombie legion."
Can you imagine the scenario of hundreds of thousands of zombies attacking you under the command of one person?

â–² brain complement scenes, pictures from the network
Real network zombies siege
On September 20, 2016, KrebsOnSecurity.com, the famous security news website, was subjected to such "zombie siege" (DDoS distributed refusal attack). î‰’ç¡ æµ” セ鞣逯 セ鞣逯 セ鞣逯 セ鞣逯 65 65 65 é” é” 65 65 Gbps.
On the same day, the French website host OVH was also besieged by Mirai's zombie, and the DDoS attack volume reached 1.5Tpbs.
What is the concept of 1.5Tbps? Lei Fengnet gives another example as a comparison:
In March 2013, a 300-Gbps attack hit a historical record and was rated as "almost European network." 1.5Tbps is three times that. Two years ago, two or three European countries were paralyzed.
According to occupants, the total bandwidth of some domestic small and medium-sized cities does not necessarily have 500G. That is to say, if there is such a large flow of traffic to the IP of a certain city, the city will probably cut off the network.
This is the power of Mirai.
On September 30, 2016, what did the author of the Mirai author Senpai do? - He published the source code of Mirai to the Internet, and everyone can make his own Mirai botnet based on this code, and they have the opportunity to command thousands of "net zombies" to attack the city.
"I'm just making money. Now that many people are paying attention to the Internet of Things, it's time to announce Mirai." When releasing Mirai, Senpai seemed calm.
More than 20 days later, the entire United States experienced a large-scale network disconnect. The reason was that the DDN, a domain name analysis service provider, was attacked by powerful DDOS. The researchers discovered hundreds of thousands of attack sources. All sources point to the Mirai botnet.
Since then, the number of devices infected with Mirai on the Internet has dramatically increased. According to statistics, the first month has doubled. The public Mirai has been collected and marked by people for thousands of times.
IoT Zombie Concealed
The zombies that plague the Internet of Things are not only Mirai.

â–² Vampires, Zombies, Zombies... Variety
Before Christmas last year, on the morning of December 21, the United States observed an attack initiated by a botnet named "Leet" with traffic up to 650Gps.
After that, there was a botnet "Amnesia" that was specifically targeted at DVR hard disk recorder infections. According to the scan results, more than 700,000 targets were enveloped under its threat.
A few weeks ago on March 20, a new botnet named Brickerbot, similar to the Mirai botnet, appeared. Unlike the former, it would directly destroy the invaded devices (permanently destroyed). For example, if the camera at the intersection is damaged, there are ways to make your smart rice cooker blow up...
A variety of botnets, which invade the world at their own pace, will also fight for an attack target.
A recent botnet family named "Bashlight" is in fierce competition with Mirai. Because the infection targets are roughly the same, the methods used are similar, and both involve the busybox vulnerabilities used by the embedded Linux system on which the device is running.
Then Mirai shot, it encrypted the traffic between the infected device and the command control server, and took over Bashlight-infected devices. It also patched the devices to prevent them from being infected by competitors again.
When a prey is bitten by a vampire and zombie at the same time, will he be infected with a vampire or a zombie? The answer, of course, is to see who's toxic. When a device is infected by two botnets at the same time, who can get control? Who sees the technology NB.
Currently, nearly 100,000 devices in the Bashlight botnet have been controlled by Mirai. Obviously Mirai is even better.
"Go away, this is Laozi's prey."
Transfer
In this way, tens of thousands of vulnerable devices in the cyber world are constantly being attacked and divided by various botnets. Each botnet wants to control more control of the Internet of Things devices. In a chaos, two "zombie families" came to the fore, fighting for the name of the hegemony Internet of Things.
Their name is, Mirai and Hajime. Coincidentally, the meanings in Japanese are: "Future" - "Start"
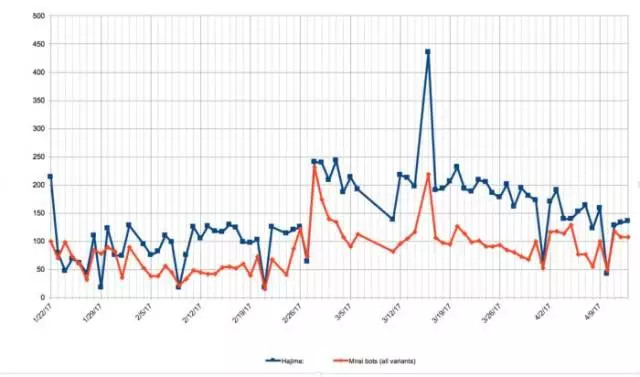
â–² Blue is Hajime, Orange is Mirai
Both of these zombie worms travel in similar ways, using networked devices that do not take protective measures (such as a network router opening a remote login port and using the default password) for propagation.
However, Hajime's actions are more secretive and the technology is more advanced.
Unlike Mirai, which uses hard-coded addresses for commanding and controlling C&C servers, Hajime builds on a peer-to-peer network. In other words, Mirai may find behind-the-scenes manipulators (C&C servers), and Hajime's behind-the-scenes manipulators are hidden among any infected person, making them harder to trace and more difficult to destroy.

â–² It's like killing virus Smith in the movie "The Matrix"
Security company Symantec told Lei Fengwang (public number: Lei Feng network) that in the past few months, Hajime has spread rapidly. It is conservatively estimated that the number of infected devices in the world has reached tens of thousands of units, and China is one of the infected markets.
â–² Hajime infected areas are distributed, Source: Symantec Security Announcement
However, security researchers were surprised to find that Hajime does not perform malicious operations and does not include any Ddos functionality and code, but instead pushes a message to infected devices every 10 minutes:
We are the white hat of the protection system. We will demonstrate important information through this method!
Hajime creator
Contact closure
Please be vigilant!
Even Hajime's squatters rushed to step on the port to attack Mirai's attacking ports (23, 7547, 5555, and 5358 visits). Closing these ports would effectively organize the device to be infected by Mirai. !
No one knew who Hajime was, but he used his own way on the Internet of Things to help the device block Mirai's infection.
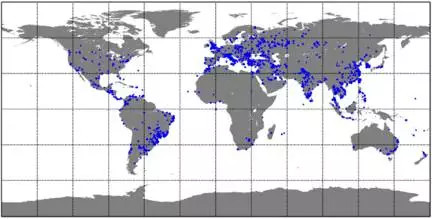
â–²Hajime global infection
Controversial White worm in white hat?
Hajime is not the first worm to call justice guards trying to protect vulnerable IoT devices.
From 2014 to 2015, Symantec discovered a software called Linux.Wifatch Worm. The software was written by the white team and is similar to Hajime's intent to provide security protection for IoT devices.
Isn't this the Spiderman or Death Knight's school in the super hero movie? - 牎 å¿ å¿ å¿ æ—¢ æ—¢ æ—¢ æ—¢ æ—¢ æ—¢
Just as the superpowers in the film are controversial, this white worm is also controversial.

â–² Spiderman's Justice and Darkness, picture source "Spider-Man 3"
Some people think that Hajime's method of forcibly providing protection is not legal, and it is hard to save one day that Hajime's author is anti-Ge.
According to Hajime's code, manufacturers can open shell scripts at any time on people-infected devices in the network. Thanks to the use of modular code, designers can add new features at any time. Once the creators change their minds and plan to do something, they can immediately transform the infected device into a huge malicious botnet.
Some people think that this is a good thing. Since some irresponsible vendors are inaction and people are powerless about botnets, why can't they treat them as others?
Even some security researchers volunteered to help Hajime. In a study on Hajime, security personnel discovered vulnerabilities in the Hajime worm and provided a quality assurance report free of charge, providing signatures to detect these vulnerabilities. Since then, Hajime has indeed repaired these flaws one by one.
In the movie "Spider-Man 3," Spider-Man was tempted by alien creatures to become Dark Spider-Man. After experiencing a series of encounters, he decided to tear away the darkness and return to the essence. In the online world of superpower hackers, they also face the lure of money, greed, etc. They can choose to become "superheroes" or to become evil thugs. In any case, other people's doubts and self-human torture can not be avoided. .
Author: Xie unitary, Lei Feng network of network security.
Paperlike Screen Protector For IPad
Paperlike Screen Protector,iPad Paperlike Screen Protector,Paperlike Screen Protector iPad
Shenzhen Jianjiantong Technology Co., Ltd. , https://www.morhoh-sz.com