With the development of wireless communication technologies, people are increasingly demanding data transmission rates. Large Scale Antenna System (Massive MIMO) [1] has many performance advantages, such as more stable channels, better predictability of channels, and more orthogonal channels between base stations and users. And the antenna gain increases linearly with the increase of the number of antennas [2], which has aroused people's interest in recent years. Massive MIMO has become one of the key candidate technologies for 5G communication [3].
Massive MIMO refers to a system in which a base station is equipped with hundreds or even more antennas. This system has considerable advantages in terms of physical layer security due to the large number of antennas, that is, a large-scale antenna array can effectively combat passive eavesdropping. Physical layer security can provide an effective security mechanism for wireless communications, which can alleviate the complexity of late-stage confidentiality protocols and effectively compensate for their performance. The so-called passive eavesdropping is that the eavesdropper only listens to the transmission information of the legitimate user during the eavesdropping process, and does not take active interference. When there is passive eavesdropping in Massive MIMO, the system's secret channel capacity will still increase with the number of antennas, that is, Massive MIMO will not be affected by passive eavesdropping [1]. In Massive MIMO, eavesdroppers must be passively switched to active eavesdropping mode to attack large-scale antenna array systems for the purpose of eavesdropping [4]. The so-called active eavesdropping is that the eavesdropper takes active interference in order to improve the eavesdropping performance during the eavesdropping process. The weakness of the large-scale antenna array system operating in the Time Division Duplex (TDD) mode is the channel estimation phase. The active eavesdropping can utilize the weak point of the system to transmit the same pilot sequence as the legitimate user in the channel estimation phase. The base station cannot accurately distinguish the legitimate user from the eavesdropping user, and the base station will simultaneously send the information to be sent to the legitimate user to the eavesdropping user. Today's communication is no longer just a telephone or messaging service. A series of online payment, such as Alipay and WeChat payment, has become a daily payment tool, ensuring the security of wireless communication is becoming more and more important. Effective detection of active eavesdropping in Massive MIMO is an important issue to be solved. The study of pilot sequences is given in [5], but the case of large-scale antenna arrays is not discussed, and the detection eavesdropping scheme is not given. Reference [6] gives an active eavesdropping scheme based on pilot sequence detection, but this scheme requires a specific pilot sequence to detect.
In order to solve the above problems, this paper proposes a specific scheme for detecting active eavesdropping in a large-scale antenna array. This scheme considers a large-scale planar antenna array operating in the TDD mode under the Rice channel. The eavesdropping detection scheme proposed in this paper does not need to design a specific pilot. Just know the legitimate user's Rice factor and the base station receiving noise power, and then construct a decision object based on the signal received at the base station, set the judgment value, and detect whether the eavesdropping exists. . The simulation results show that the performance of the detection scheme is not affected by the location change of the eavesdropping user, and the detection performance of the system increases as the number of antennas increases.
1
System model
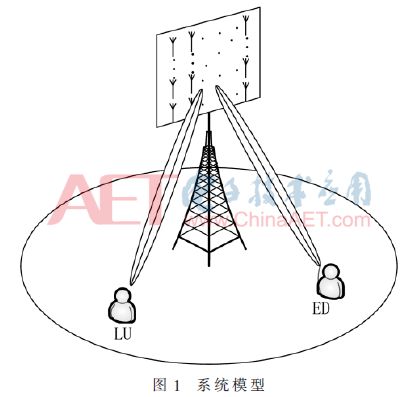
The system model studied in this paper is shown in Figure 1. The base station (BS) and the legitimate user (Legitimate User, LU) work in TDD mode. Assume that there is an Eavesdropper (ED) in the system. The base station adopts an M×N uniform planar antenna array, and the legal user and the eavesdropping user are respectively equipped with a single antenna. In addition, the system studied in this paper is in the Rice channel, and hLU and hED are used to represent the channel between the base station and the legitimate user and the eavesdropping user. The above channel can be expressed as [7]:
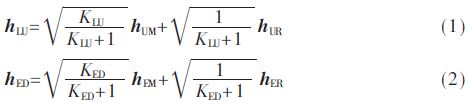
Among them, KLU and KED are the K factor of the Rice channel, that is, the ratio of the power of the main signal to the variance of the multipath component [8]; hUM and hEM respectively represent the deterministic component of the Rice channel between the base station and the legitimate user and the eavesdropping user. hUR and hER represent the corresponding random components, both of which obey the complex Gaussian distribution with a mean of 0 and a covariance matrix of I, ie hi~CN(0,I), i=UR, ER, and different users The random components are independent of each other. In this paper, the base station adopts a uniform rectangular antenna array, and the deterministic components hUM and hEM of the Rice channel can be expressed as [9]:

It is assumed in the equations (5) and (6) that the line and column pitch of the antenna are both half of the carrier wavelength.
In the TDD communication mode, in order to achieve coherent downlink transmission with a legitimate user, the base station needs to estimate the channel through the training sequence. During the training phase, legitimate users send a series of pilot signals to the base station for channel estimation. Let the legitimate user's transmit power be pLU. When there is no active eavesdropping user, the signal received by the base station can be expressed as:

02
Testing plan
According to formula (9) and formula (10), the signal received by the base station has obvious difference when the eavesdropping user exists and does not exist. Therefore, according to this, a detection scheme of the eavesdropping user is proposed, and the scheme assumes the legal user's The sigma coefficient KLU and the base station noise power NBS can be estimated from parameters and the detection is done by the base station. In the detection, let pLU=1, pED=1, the base station constructs the detection object from the received signal r:
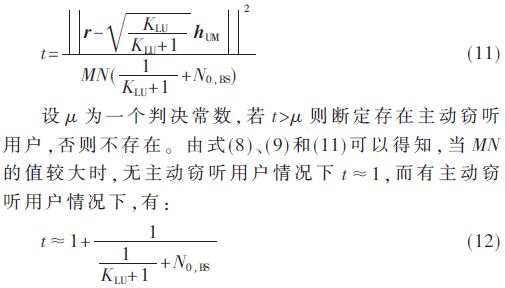
Therefore, the setting of μ should be slightly larger than 1, and the setting of μ value will directly affect the detection effect.
It can be seen from equations (8) and (11) that when there is no active eavesdropping user, t is a scaled chi-square distribution with a degree of freedom of 2MN, namely:

3
Simulation results

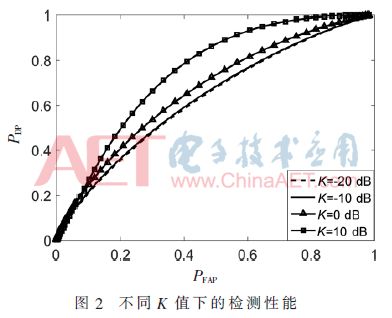
As shown in Figure 2, the first simulation example verifies the effect of the Rice Factor K on the ROC curve. In this example, KLU = KED = -20 dB, -10 dB, 0 dB, and 10 dB. It can be seen from the figure that the detection performance of the eavesdropping user increases with the increase of the K value, that is, the detection method proposed in this paper has better performance when the deterministic component accounts for a higher proportion of the channel coefficient.
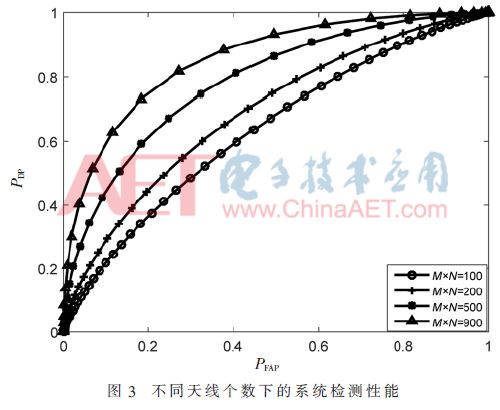
The second example is to verify that the system's detection performance is affected by the number of antennas. Figure 3 shows the ROC curves for antennas of 100, 200, 500 and 900. It can be seen from the figure that the detection performance of the system increases significantly with the increase of the number of antennas, so the large-scale antenna array helps to improve the system performance.


4
in conclusion
This paper proposes a method for detecting active eavesdropping users for the time division duplex system in Rice channel. The system base station is equipped with a large-scale planar rectangular array antenna, and a legitimate user and an eavesdropping user are respectively equipped with one antenna. In this paper, the two-dimensional channel model is first transformed into a one-dimensional vector model, which simplifies the planar antenna array problem under the Rice channel. Secondly, according to the characteristics of the signals received by the base station, the detection object is constructed. The detection object obeys the scaled chi-square distribution when there is no active eavesdropping user, and obeys the non-central scaled chi-square distribution when actively eavesdropping the user, so that a closed expression of the false positive probability and the detection probability can be obtained. It can be known from the misjudgment and detection probability expression that the scheme only needs to estimate the Les channel factor and the base station noise power, and both do not depend on the spatial orientation of the user, so the method can effectively detect all eavesdropping users in the three-dimensional space. . The simulation results show that the performance of the eavesdropping detection scheme proposed in this paper increases with the number of antennas and the Rice factor, so it is suitable for large-scale antenna arrays.
Battery Cable,Lithium Battery Cable,Battery Cable Connector,Silicone Cover Wire Harness
Dongguan ZhiChuangXing Electronics Co., LTD , https://www.zcxelectronics.com