Among the 25 best inventions in 2017 released by Time magazine, the iPhone X is on the list. In addition to removing the Home button, the next-generation biometric verification technology Face ID is undoubtedly one of the most revolutionary designs since the release of the iPhone in early 2007.
In fact, since the launch of Face ID, the voice of doubt has not stopped. Recently, two cracked Face ID events occurred, namely, the Vietnam ID 3D mask unlocking Face ID and a child unlocking the Face ID of the mother's mobile phone, which provoked various doubts and the technical insecurity was continuously rendered.
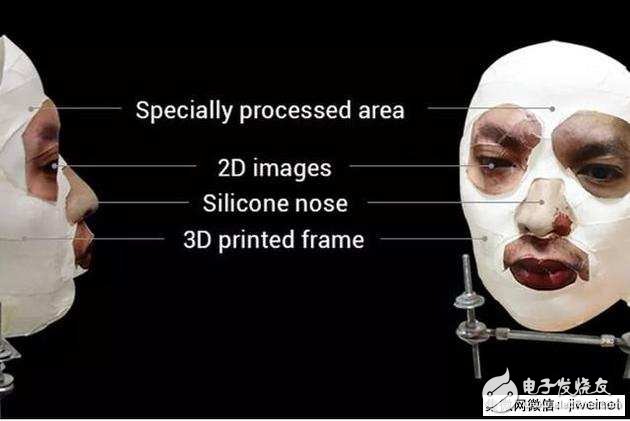
How familiar is this scene. When Touch ID fingerprinting was launched on the iPhone 5s in 2013, the experience of the fingerprint scanner in the whole industry was not perfect. After that, the message of successfully unlocking the mobile phone with high-definition fake fingerprint model was frequently used.
Cracking and questioning doesn't start with Touch ID, it doesn't stop at Face ID, it seems to be continually cracked and then gradually revised. It is the ultimate fate of these emerging biometric technologies, especially the automatic identification technology involving privacy and security. .
And this time, a little more special, Face ID reveals a problem: the potential security "threat" of your phone has even come from your children, parents, siblings and "some" to get your phone and provide you with accurate face The person who is the information, that is, the person closest to you.
As for the cracking incident that just broke out, the child cracked the mother's mobile phone. It can be understood that Apple CEO Cook mentioned it when releasing the iPhone X, although the possibility of unlocking the Face ID is one in a million (Touch) The probability of ID is one in 50,000, but it may be invalid in people with similar looks, especially in twins. The probability of error increases a lot.
For the security research team in Vietnam, their method of cracking is too cumbersome considering time and cost. In order to obtain a mobile phone, it is also necessary to obtain accurate face information of the mobile phone user, not to mention the use of 3D printing technology in the production of a special mask, although the cost is not too high, but not for a normal user. Reality, because the cost and cumbersome process cannot be equal to the benefits obtained, but it is more likely that a specific target user such as a well-known politician, star, billionaire, who has a lot of public face information, is a potential attack. Goals, but how likely is it to get their phones at the same time?
This at least shows that in the field of face recognition, the security of it is conditional; but from another perspective, the more you crack, the more critical the condition determines your Face ID. The probability of being cracked is indeed very low.
The security protection settings of mobile phones are still not guaranteed to be foolproof, and it is impossible to completely crack them. However, with the advancement of technology, the cost of cracking has become higher, exceeding the gains that may be obtained, and the probability of being cracked is thus reduced as much as possible. If it really costs a lot of money to crack a person's mobile phone, it is estimated that there is no security device to resist.
Professor Calestous Juma of the Bellver Center for Science and International Affairs at Harvard Kennedy School, in the book "Innovation and its Enemy: Why People Resist New Technologies," mentions the drive behind the resistance to new technologies. Power is a sense of loss. People don't just oppose these technologies because they are brand new or they don't know anything about them. They try to resist a sense of loss. The key point here is that resistance to new technologies is often driven by perception rather than objective facts.
In other words, our sense of insecurity is not entirely a technical issue.

Previous reports from various sources confirmed that Apple made the decision to cancel the Touch ID before the iPhone X was officially mass-produced. In order to realize a comprehensive screen, in the known apple preparation scheme, a back fingerprint recognition scheme, a screen fingerprint recognition scheme and a face recognition scheme are mainly included. Facial recognition is obviously one of the most secure settings in terms of jumping. Screen fingerprinting technology is not yet mature. Apple has chosen the Face ID in mass production to eliminate this most popular scheme. It is inevitable that Face ID will leave an impression: This is the second best alternative. Coupled with the fact that Face ID was shown for the first time at the press conference, it was said that it was unfavorable to succeed in the past.
However, in addition to the subjective impressions of the immature technology left in the previous period, many of the questions raised in the late Face ID are more due to our lack of understanding of some of its technical principles.
Face ID is a 3D-based facial recognition that uses an infrared camera and high-precision distance sensing to work together to sample the face in three dimensions. So in simple terms, it is often referred to as simple transposition and styling, 2D face images of screen remake, human skin masks, and even plastic faces that are difficult for human eyes to recognize. These common common concerns are in professional The designer's internal testing can of course be foreseen and corrected.
The cracked one does not involve any of the above situations. In addition to the power of the sighing gene, there is also the "mysterious" power from the 3D fake face black technology.
Face recognition technology is no longer a new topic. As a relatively mature and reliable biometric technology, it is widely used in the fields of face verification, human-computer interaction, public area monitoring, and security counter-terrorism. There are more application scenarios to be expanded. In addition, although 3D structured light technology is currently relatively versatile, it is also the first time it has been applied to portable mobile terminals such as mobile phones. Therefore, our understanding of this technology needs to be deepened with the expansion of the application scenario, and the technology itself is not perfect, and it will take time to verify.
Fingerprint unlocking, which has been proven and widely used, is more reliable than Face ID, which has just been applied to mobile phones. Fingerprints that are unique to each other and that do not change over the years do not exist, similar family or twins, and concerns about recognition errors as the appearance changes. There are different characteristics and differences of different biometric technologies, and some of them come from the future human-computer interaction to get rid of the interface interaction, resulting in an insecure upgrade.
Touch ID is not as good as Face ID in terms of the convenience of the operation process. However, the drawback of face recognition is that it may be used without knowing it. In the field where security and privacy are most valued, Touch ID needs people. The interaction of the machine interface increases the autonomous controllability of the person to a certain extent, which may increase the sense of security.
In fact, whether it is traditional digital passwords, graphic passwords, fingerprint recognition and face recognition, they are all ways of human-computer interaction. But it is like when we have adapted to fingerprint unlocking, even if the news of fingerprint cracking is not new, we can't completely return to using traditional passwords. It is undeniable that face recognition is free from the limitations of interface interaction and is better than fingerprint recognition. A biometric authentication method that is more responsive to the development trend of human-computer interaction. In the future, a variety of specific modes of operation will be fused, making the boundaries between people and computers increasingly blurred.
Every time the technical cracking is eagerly linked to "fear" and "worry", the insecurity of over-rendering technology is unfair to the new technology itself. The changes brought about by new technologies require a process. Old habits have been developed, and the solutions given by new technologies are not perfect and not popular enough, but this should not be a reason for vetoing and resisting new technologies. .
In the book Principles of Marketing, Kotler said: "One of the most dramatic forces for changing human destiny is technology. Every new technology is a kind of 'creative destruction' power, transistors make the vacuum industry decline, copiers The carbon paper industry is declining. New technologies have created new markets and opportunities, and new technologies will eventually replace old technologies. If the old industries ignore or even resist new technologies, they will decline."
Whether it is the subjective assumption of lack of cognition, or simply sticking to tradition and not being able to generate enough trust in new technology, you are deepening your own insecurity. The true sense of technical security is based on in-depth technical cognition and the inherent security upgrade of technology.
In other words, don't think too much, except to manage your child, no one has to crack your phone.
AKH-0.66/K-Φ series Electricity factory class 0.5 current transformer for automatic system are mainly used in reconstructing projects of urban and rural power grids. class 0.5 current transformer has the advantages of small size, high accuracy, strong load capacity, easy installation, etc.split core open type current transformer save the manpower, material resources and financial resources and improve the efficiency of users.
AKH-0.66K series Current transformer relay for automatic system are mainly used in renovation projects of urban and rural power grids. current transformer relay can be mounted easily without removal of primary bus bar. lcurrent transformer also can be operated with electricity, split core current transformer price prevents the normal utilization of electricity. Thus, they save the manpower, material resources and financial resources and improve the efficiency of users.This series match with relay protection, measuring and metering equipment.

Split Core Current Transformer,Open Type Current Transformer,Split Core Ac Current Transducer,Ac Split Core Current Transformer
Jiangsu Acrel Electrical Manufacturing Co., LTD. , https://www.acrel.com.pk