The function of the ICMP protocol is very important. In the study of network protocols, this part of the knowledge is also the focus of our explanation. So how does the ICMP protocol work and how is the workflow completed? Let's take a closer look at the validation issues in this area. First we have to define the definition of ICMP.
Introduction to ICMPFor those who are familiar with the Internet, ICMP is no longer familiar. It works like the IP protocol in the network layer of the ISO model. Its full name is: Internet Control Message Protocal. Its main role in the network is:
- Host detection
- Route maintenance
- Routing
- flow control
There are many ways to detect a host, BANNER for some services on the host, some applications used, or tools to detect hosts, such as NMAP, which has a simple estimate of the host on the WEB. The following is to use the ICMP protocol to detect the host, mainly to understand the ICMP protocol, the most important thing here is the ICMP protocol.
Protocol Analysis - Detailed ICMP Protocol Decoding
ICMP is called Internet Control Message Protocol. The Chinese name is Internet Control Message Protocol. It works at the network layer of the OSI and reports errors to the source host in the data communication. ICMP enables fault isolation and fault recovery.
The network itself is unreliable. During the network transmission, many unexpected events may occur and the data transmission fails. The network layer IP protocol is a connectionless protocol, it does not deal with network layer transmission failures, and the ICMP protocol at the network layer just makes up for the lack of IP. It uses the IP protocol for information transfer to packets. The source node in the middle provides error information feedback that occurs at the network layer.
ICMP provides multiple types of messages to provide source layer nodes with network layer fault information feedback. Its message types can be summarized into the following five categories:
Diagnostic message (type 8, code 0; type 0, code 0);
Destination unreachable message (type 3, code 0-15);
Redirect message (type 5, code 0-4);
Timeout message (type 11, code 0-1);
Information message (type 12-18).
Detailed decodingUsing the Kelai network analysis system to capture the data packet, we get the information of the ICMP echo message, as shown in Figure 1.
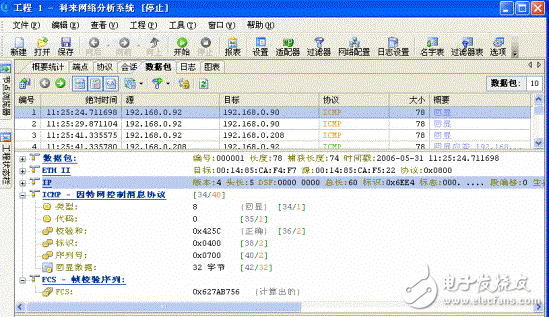
The full name of ICMP is InternetControlMessageProtocol. From the technical point of view, ICMP is a "error detection and reward mechanism", the purpose is to enable us to detect the connection status of the network, and also ensure the accuracy of the connection, its function There are:
â—†Detect if the remote host exists.
â—† Establish and maintain routing data.
â—† Redirect the data transfer path.
â—† Data flow control.
ICMP is in communication, mainly through different categories (Type) and code (Code) to allow the machine to identify different connection conditions. Common categories are listed in the following table:
ICMP is a very useful protocol, especially when we want to judge the status of the network connection. Let's take a look at the commonly used ICMP examples to better understand the function and role of ICMP.
The importance of the ICMP protocolThe ICMP protocol is extremely important for network security. The characteristics of the ICMP protocol itself make it very easy to be used to attack routers and hosts on the network. For example, in August 1999, Hisense Group "rewarded" 500,000 yuan test firewall In the process, its firewall suffered ICMP attacks up to 334,050 times, accounting for more than 90% of the total number of attacks! It can be seen that the importance of ICMP can never be ignored!
For example, the "PingofDeath" attack can be initiated to the host by using the maximum size of the ICMP packet specified by the operating system not exceeding 64 KB. The principle of the "PingofDeath" attack is: if the size of the ICMP packet exceeds 64 KB. For a limited time, the host will have a memory allocation error, causing the TCP/IP stack to crash, causing the host to crash.
In addition, sending ICMP packets to the target host for a long time, continuously, and in large quantities will eventually make the system paralyzed. A large number of ICMP packets will form an "ICMP storm", which makes the target host consume a lot of CPU resources and is exhausted.
ICMP protocol checksum algorithm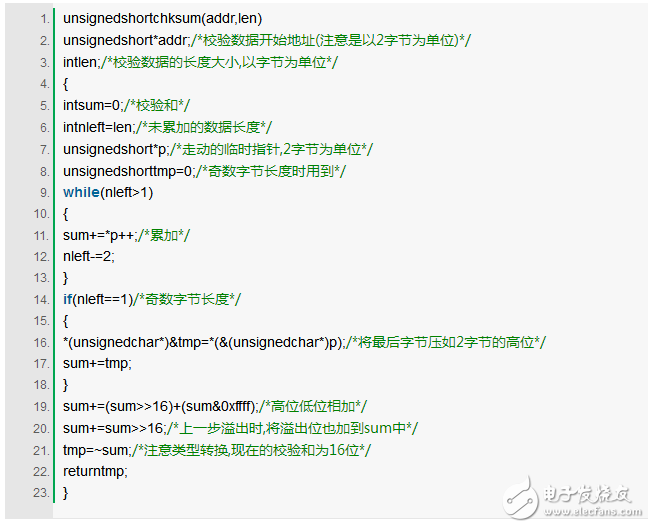
We often use the ICMP protocol in the network, but we are not aware of it? For example, we often use the Ping command to check the network is not available. The process of "Ping" is actually the process of working with the ICMP protocol. Are there other network commands such as Tracert's Tracert command based on the ICMP protocol?
ZGAR AZ MC Disposable
ZGAR electronic cigarette uses high-tech R&D, food grade disposable pod device and high-quality raw material. All package designs are Original IP. Our designer team is from Hong Kong. We have very high requirements for product quality, flavors taste and packaging design. The E-liquid is imported, materials are food grade, and assembly plant is medical-grade dust-free workshops.
Our products include disposable e-cigarettes, rechargeable e-cigarettes, rechargreable disposable vape pen, and various of flavors of cigarette cartridges. From 600puffs to 5000puffs, ZGAR bar Disposable offer high-tech R&D, E-cigarette improves battery capacity, We offer various of flavors and support customization. And printing designs can be customized. We have our own professional team and competitive quotations for any OEM or ODM works.
We supply OEM rechargeable disposable vape pen,OEM disposable electronic cigarette,ODM disposable vape pen,ODM disposable electronic cigarette,OEM/ODM vape pen e-cigarette,OEM/ODM atomizer device.

Disposable E-cigarette, ODM disposable electronic cigarette, vape pen atomizer , Device E-cig, OEM disposable electronic cigarette
ZGAR INTERNATIONAL(HK)CO., LIMITED , https://www.szdisposable-vape.com